🛠️139,445 SMB
Checklist
Enumerate Hostname -
nmblookup -A [ip]List Shares
smbmap -H [ip/hostname]echo exit | smbclient -L \\\\[ip]nmap --script smb-enum-shares -p 139,445 [ip]
Check Null Sessions
smbmap -H [ip/hostname]rpcclient -U "" -N [ip]smbclient \\\\[ip]\\[share name]
Check for Vulnerabilities -
nmap --script smb-vuln* -p 139,445 [ip]Overall Scan -
enum4linux -a [ip]Manual Inspection
smbver.sh [IP] (port)[Samba]check pcap
Tools
nmblookup- collects NetBIOS over TCP/IP client used to lookup NetBIOS names.smbclient- an ftp-like client to access SMB sharesnmap- general scanner, with scriptsrpcclient- tool to execute client side MS-RPC functionsenum4linux- enumerates various smb functionswireshark
Details
Enumerate Hostname
nmblookup
nmblookup -A [IP]
-A- look up by IP address
Example:
List Shares
smbmap
smbmap -H [ip/hostname]
This command will show you the shares on the host, as well as your access to them.
Example:
If you get credentials, you can re-run to show new access:
smbclient
echo exit | smbclient -L \\\\[ip]
exit takes care of any password request that might pop up, since we’re checking for null login
-L- get a list of shares for the given host
Example:
Dump All Files
nmap
nmap --script smb-enum-shares -p 139,445 [ip]
--script smb-enum-shares- specific smb enumeration script-p 139,445- specify smb ports
Example:
Check Null Sessions
smbmap
smbmap -H [ip/hostname] will show what you can do with given credentials (or null session if no credentials). See examples in the previous section.
rpcclient
rpcclient -U "" -N [ip]
-U ""- null session-N- no password
Example:
From there, you can run rpc commands.
smbclient
smbclient \\\\[ip]\\[share name]
This will attempt to connect to the share. Can try without a password (or sending a blank password) and still potentially connect.
Example:
Check for Vulnerabilities
nmap
nmap --script smb-vuln* -p 139,445 [ip]
--script smb-vuln*- will run all smb vulnerability scan scripts-p 139,445- smb ports
Example:
Overall Scan
enum4linux
enum4linux -a [ip]
-a- all enumeration
Example output is long, but some highlights to look for:
output similar to nmblookup
check for null session
listing of shares
domain info
password policy
RID cycling output
Manual Inspection
Samba
ngrep is a neat tool to grep on network data. Running something like ngrep -i -d tap0 's.?a.?m.?b.?a.*[[:digit:]]' port 139 in one terminal and then echo exit | smbclient -L [IP] in another will dump out a bunch of info including the version.
rewardone in the PWK forums posted a neat script to easily get Samba versions:
When you run this on a box running Samba, you get results:
When in doubt, we can check the smb version in PCAP. Here’s an example Unix Samba 2.2.3a: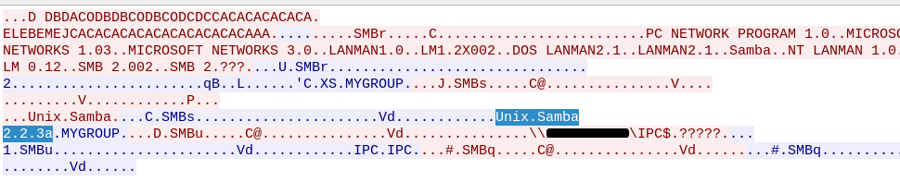
Windows
Windows SMB is more complex than just a version, but looking in wireshark will give a bunch of information about the connection. We can filter on ntlmssp.ntlmv2_response to see NTLMv2 traffic, for example.
Last updated